Privacy Invasion
"The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized." ---Fourth Amendment to the Constitution
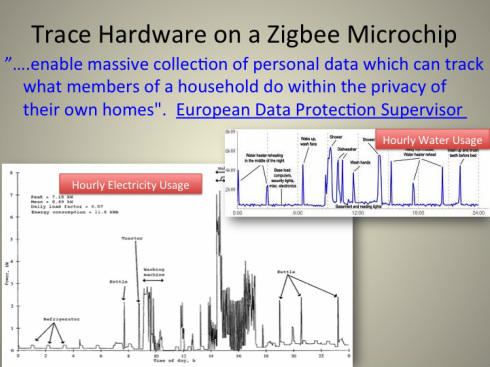
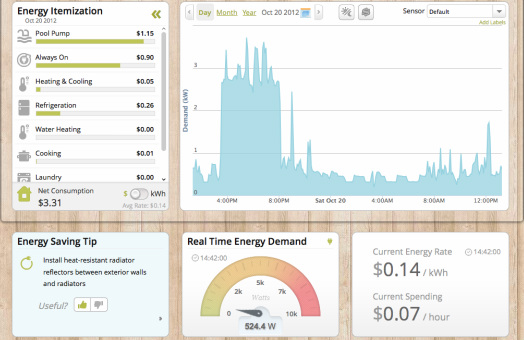
Smart Meters measure electricity usage in your home using a transmitting, wireless computer. Posing as a 'smart' and helpful device, it collects data of your family's daily habits and activities. This information is permanently stored as Big Data. Who has access to this Big Data?
By definition a surveillance device, the Smart Meter violates Federal and State wiretapping laws by recording and storing Big Data of private personal activities and behaviors without direct consent or knowledge. Big Utilities promise to keep this data safe and secure. The only secure data is data never collected.
Smart Meters measure electricity usage in your home using a transmitting, wireless computer. Posing as a 'smart' and helpful device, it collects data of your family's daily habits and activities. This information is permanently stored as Big Data. Who has access to this Big Data?
By definition a surveillance device, the Smart Meter violates Federal and State wiretapping laws by recording and storing Big Data of private personal activities and behaviors without direct consent or knowledge. Big Utilities promise to keep this data safe and secure. The only secure data is data never collected.
|
Orwellian Smart Meters
They do much more than just show how much electricity you use. The Smart Meters is watching you. - -Jerry Day explains. (6/2011) |
|
|
Appliances Have Data Signatures
This image from IEEE Spectrum Magazine reports that "of more than 9,000 consumers polled in 17 countries, about one-third said they would be discouraged from using energy-management programs, such as smart metering, if it gave utilities greater access to data about their personal energy use." They go on to say that "each appliance—the refrigerator, kettle, toaster, washing machine—has its own energy fingerprint, or 'appliance load signature,' that a smart meter can read. Anyone who gets hold of this data gets a glimpse of exactly what appliances you use and how often you use them. |
|
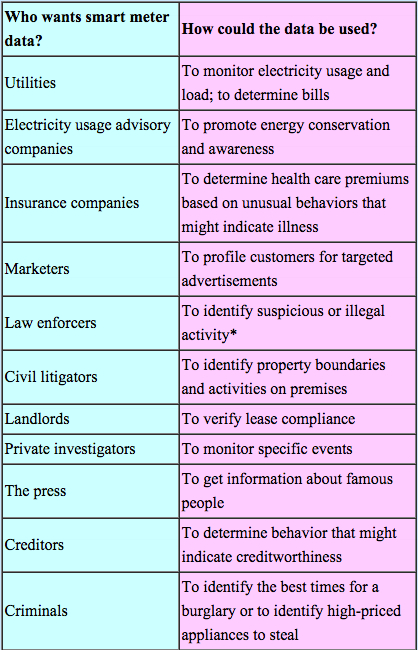
Do You Really Have "Nothing to Hide"?
"Such data might be used in ways that raise privacy concerns. For example, granular Smart Grid data may allow numerous assumptions about the health of a dwelling’s resident in which some insurance companies, employers, newspapers (when regarding public figures), civil litigants, and others could be interested. Most directly, specific medical devices may be uniquely identified through serial numbers or MAC addresses, or may have unique electrical signatures; either could indicate that the resident suffers from a particular disease or condition that requires the device."
|
Source: ”Potential Privacy Impacts that Arise from the Collection and Use of Smart Grid Data,” National Institute of Standards and Technology, Volume 2, pp. 30–32, Table 5-3.
|
|
Purposeful Unconstitutional Warrant-less Search
"The Smart Grid will greatly expand the amount of data that can be monitored, collected, aggregated, and analyzed. This expanded information, particularly from energy consumers and other individuals, raises added privacy concerns. For example, specific appliances and generators may be identified from the signatures they exhibit in electric information at the meter when collections occur with great frequency as opposed to through traditional monthly meter readings. This more detailed information expands the possibility of intruding on consumers’ and other individuals’ privacy expectations. The Supreme Court in Kyllo (533 U.S.) clearly reaffirmed the heightened Fourth Amendment privacy interest in the home and noted this interest is not outweighed by technology that allows government agents to “see” into the suspect’s home without actually entering the premises. The Court stated, “We think that obtaining by sense-enhancing technology any information regarding the interior of the home that could not otherwise have been obtained without physical intrusion into a constitutionally protected area, constitutes a search” and is “presumptively unreasonable without a warrant.” Source: From the Smart Grid Cybersecurity Guidelines, Sept. 2010 (pdf) |
If you can read this on your Smart phone..so can any hacker.
|